|
Mail Access Monitor for Kerio MailServer 3.2 - User Guide and FAQ
Screenshots - More Details
How Mail Access Monitor works?
It's hard to imagine an office without access to e-mail. Just as hard as finding a large company that does not have irresponsible employees who prefer exchanging e-mail messages with their friends rather than doing their job. If you are a manager, business owner or IT specialist, you have to know that there is a simple, quick and inexpensive way to take control of corporate e-mail system. Mail Access Monitor is a simple tool that analyses mail server logs and shows how much traffic is being used by e-mail, who sends and receives most messages, where the messages are being send to and if e-mail abuse takes place in your office. The program works with all popular e-mail servers (MDaemon, Kerio MailServer, Merak Mail Server, MS Exchange Server, VisNetic MailServer, CommuniGate Pro, SendMail, PostFix and QMail) and builds charts that are easy to comprehend.
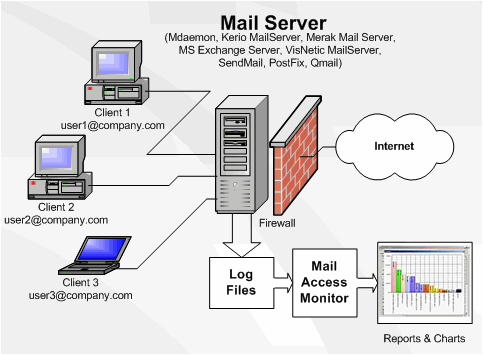
A simple glance at the chart reveals a lot of information. For example, you may find out that most outgoing e-mail messages are not related to work in any way and cost you hundreds of dollars in extra traffic a year. Or that some employees average 30-50 emails a day. Or, on the other hand, some of your sales staff members who are supposed to be proactive at approaching clients only reply to incoming messages.
The best part of Mail Access Monitor is that it starts working right after installation (which takes less then 1 minute) and frees you from having to look over employees' shoulders. As soon as employees learn that their e-mail use is being tracked and that the abusers will be punished, their productivity increases drastically. In fact, Mail Access Monitor is so effective that some Fortune 500 companies made it a mandatory policy to have the program installed in every office and branch around the globe!
Frequently Asked Questions - Mail Access Monitor for Kerio MailServer
- Mail Access Monitor's address list contains a great number of e-mail addresses that are not local
This problem occurs when you have not specified or have provided an incorrect list of local domain names. Thus, the program does not distinguish the global and local mail correctly, and therefore the number of e-mail reported addresses increases. To solve this problem: completely clean up the database (remove all the database files), provide the correct list of local domain names in the program settings, and import the log files once again.
- Outgoing traffic equals zero
This problem may occur with processing Kerio WinRoute Firewall log files. Outgoing traffic values may always equals zero because you process a http log files only. This type of log files contains only one column with traffic values and as a result, the program uses these values as Incoming Traffic. If you want to see an exact traffic figure, you should analyze a connection log files. This type of log files contains all information about incoming and outgoing traffic values.
For solving this issue you should:
- In Internet Access Monitor - open the Settings dialog, select your Data Source and open its Import Settings. Then select Connection.log in "Log Files To Import" field.
- In Kerio WinRoute Firewall - select Traffic Policy tab and configure logging (in connection.log) all of your external rules (Rules, allowing external traffic).
- Cannot create a diagram.
The diagram building procedure works based on a previously generated report. To create a diagram: select some section in the report (for instance, "By weekdays"), right-click on the column header and select the "Diagram" item in the appeared context menu.
- An "Unknown" items appears in the report
An "Unknown" items appears in the "By Users" section after import process
The problem may occur due to following reason:
If some user not authenticated on your proxy server or if UserName field is empty in log file, the program uses the "Unknown" reserved word instead of user name.
To avoid it, you should enable and configure authorisation on your proxy server or firewall.
An "Unknown" items appears in the "By Protocols" and "By Content Types" sections after import process
The problem may occur due to following reason:
During the import process the program try to associate each request with some protocol or content type. The association is carried out based on a requested file's extension. If program can't to determine a protocol or a content type, it uses the "Unknown" reserved word instead.
To avoid it, you should open the "Advanced Settings" dialog and configure the lists of protocols and content types. Then you need to reimport your log files.
An 'Unknown URL' item appears in the 'By host' section.
The problem may occur due to several reasons:
Reason 1
You use WinGate proxy server. Such error may occur sometimes due to the server's specifics in creating of log files.
Reason 2
Sometimes proxy servers do not record visited URL's. In such case, the program replaces the blank with the "Unknown URL" label
Screenshots - More Details
|



